Navigating Cybersecurity Legal Compliance Challenges
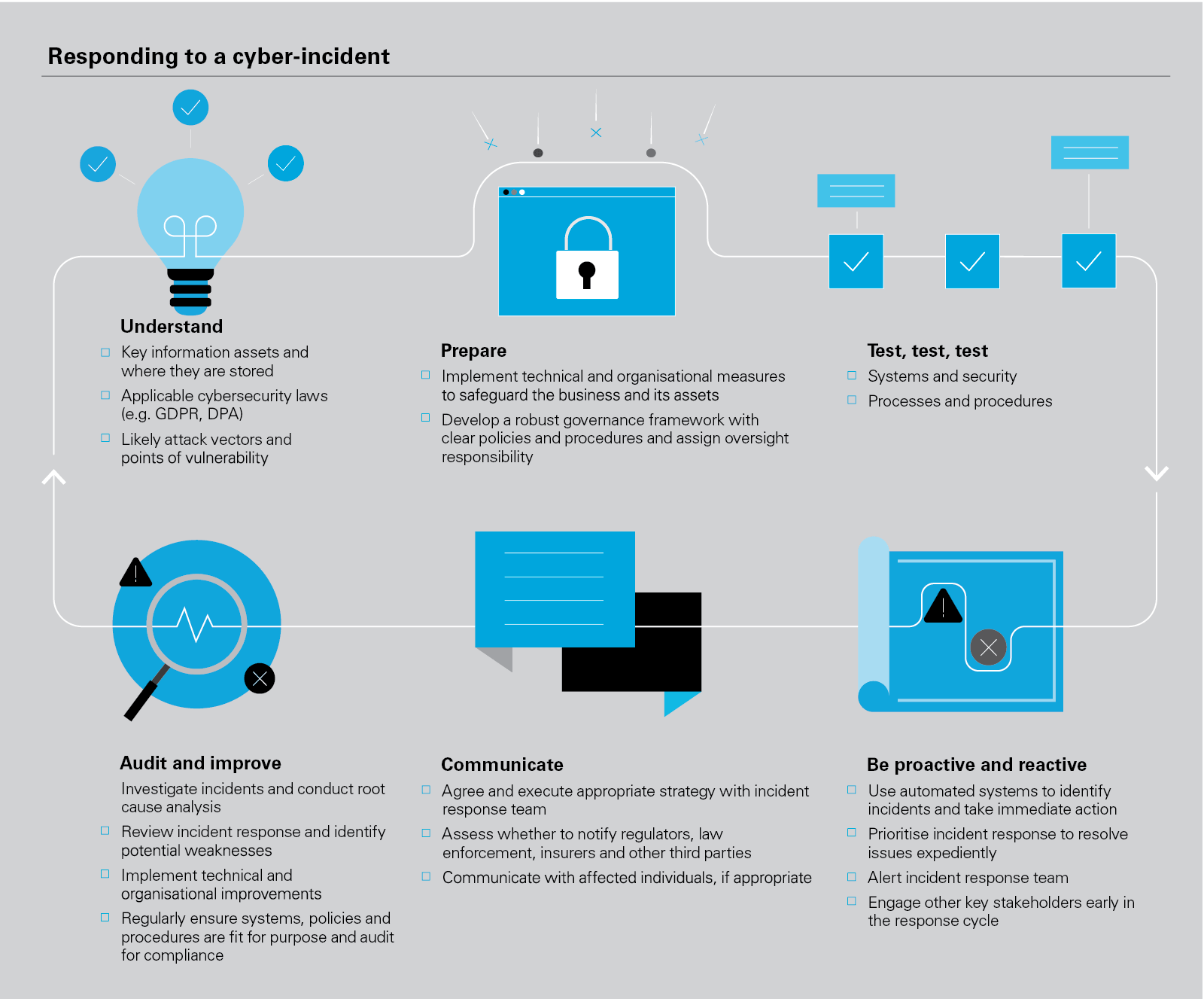

Navigating Cybersecurity Legal Compliance Challenges
Cybersecurity has become a top priority for organizations globally, with the increasing frequency and sophistication of cyber threats. Amidst this landscape, legal compliance plays a crucial role in ensuring that businesses are adequately protected and meet regulatory requirements.
Understanding the Regulatory Landscape
The realm of cybersecurity legal compliance is vast and ever-evolving. Various regulations and frameworks, such as GDPR, HIPAA, and CCPA, dictate how organizations should handle and protect sensitive information. Understanding the nuances of these regulations is essential for developing a robust cybersecurity strategy.
Data Protection and Privacy Laws
One significant aspect of cybersecurity legal compliance revolves around data protection and privacy laws. Businesses must ensure the secure handling of personal and sensitive information, obtaining proper consent for data processing, and promptly addressing any data breaches. Failure to comply can result in severe legal consequences.
Building a Comprehensive Cybersecurity Policy
To meet legal requirements, organizations need a well-defined and comprehensive cybersecurity policy. This policy should outline measures for data encryption, secure access controls, regular security audits, and incident response plans. Having a clear policy not only ensures legal compliance but also strengthens overall cybersecurity posture.
Employee Training and Awareness
Human error is a common factor in cybersecurity incidents. Legal compliance requires organizations to invest in employee training and awareness programs. Ensuring that staff understands the importance of cybersecurity, recognizing phishing attempts, and following secure practices are integral elements of compliance.
Incident Response and Reporting Obligations
Legal compliance mandates that organizations have robust incident response plans. This includes protocols for detecting, containing, and mitigating cybersecurity incidents. Additionally, regulations often impose reporting obligations, requiring organizations to promptly notify authorities and affected parties in the event of a data breach.
Third-Party Risk Management
Many businesses rely on third-party vendors for various services. Cybersecurity legal compliance extends to these relationships, necessitating thorough vetting of third-party security practices. Contracts should include clauses that hold vendors accountable for maintaining a secure environment and promptly reporting any security incidents.
Regular Security Audits and Assessments
Staying compliant requires ongoing efforts to assess and improve cybersecurity measures. Regular security audits and assessments help identify vulnerabilities, measure the effectiveness of security controls, and ensure that the organization adapts to evolving threats and regulatory changes.
Ensuring Technological Compliance
Technological compliance involves implementing cybersecurity solutions that adhere to legal standards. This includes deploying encryption tools, firewalls, intrusion detection systems, and other technologies that align with regulatory requirements. Regular updates and patches are also critical to address emerging threats.
In the dynamic landscape of cybersecurity legal compliance, staying informed and proactive is key. For a deeper dive into Cybersecurity Legal Compliance, explore Great Blog About for valuable insights and resources. Navigating these challenges requires a holistic approach that combines legal understanding, technological implementation, and ongoing diligence to protect sensitive information and uphold regulatory standards.